nRansom v1 Analysis: http://xywcloud.blogspot.com/2017/09/nransom.html
nRansom v3 Analysis: http://xywcloud.blogspot.com/2017/10/nransom-v3.html
As you can see from the title, the new ransomware called “nRansom” has been updated. But after a full analysis of nRansom v2, we only found few changes(but some of them are important)
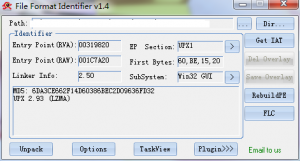
After loaded into FFI, we can find that the file is packed with UPX, so just unpack it with UPX Shell.
PureBasic Compiler? In fact, if you run it in Sandboxie, you can easily find that the file is just wrapped with “BAT2EXE”, the same as nRansom v1 did.
From the temp directory inside sandbox, we can got these files.
As for the first batch file, here is its content:
@shift /0
@shift /0
@shift /0
@echo off
md C:\Users\%USERNAME%\Desktop\nRansom2
copy nLocker2.exe C:\Users\%USERNAME%\Desktop\nRansom2
copy “C:\Users\%USERNAME%\Desktop\nRansom2\nLocker2.exe” “C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
nLocker2.exe
It just copy the embedded file to the desktop and add autorun registry.
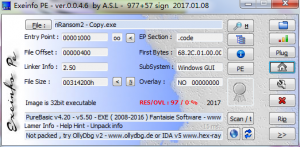
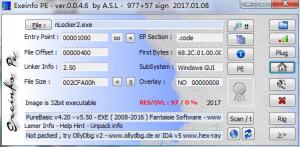
As for the executable file, let’s load into Exeinfo again.
As you can see, it’s still wrapped with “BAT2EXE”.
Now we get the final payload(nRansom2.exe), compared with nRansom v1, it’s nearly the same. The final payload is written with .NET.
After loaded into decompiler, we found that the structure is nearly the same, but some behaviors are different:
- It added a timer(5 hours), if you didn’t input correct unlock key, it will encrypt specific files in your disk(only C:\), here is a list of the encrypted files’ extension:
“.3dm”, “.3g2”, “.3gp”, “.aaf”, “.accdb”, “.aep”, “.aepx”, “.aet”, “.ai”, “.aif”, “.arw”, “.as”, “.as3”, “.asf”, “.asp”, “.asx”, “.avi”, “.bay”, “.bmp”, “.cdr”, “.cer”, “.class”, “.cpp”, “.cr2”, “.crt”, “.crw”, “.cs”, “.csv”, “.db”, “.dbf”, “.dcr”, “.der”, “.dng”, “.doc”, “.docb”, “.docm”, “.docx”, “.dot”, “.dotm”, “.dotx”, “.dwg”, “.dxf”, “.dxg”, “.efx”, “.eps”, “.erf”, “.fla”, “.flv”, “.idml”, “.iff”, “.indb”, “.indd”, “.indl”, “.indt”, “.inx”, “.jar”, “.java”, “.jpeg”, “.jpg”, “.kdc”, “.m3u”, “.m3u8”, “.m4u”, “.max”, “.mdb”, “.mdf”, “.mef”, “.mid”, “.mov”, “.mp3”, “.mp4”, “.mpa”, “.mpeg”, “.mpg”, “.mrw”, “.msg”, “.nef”, “.nrw”, “.odb”, “.odc”, “.odm”, “.odp”, “.ods”, “.odt”, “.orf”, “.p12”, “.p7b”, “.p7c”, “.pdb”, “.pdf”, “.pef”, “.pem”, “.pfx”, “.php”, “.plb”, “.pmd”, “.pot”, “.potm”, “.potx”, “.ppam”, “.ppj”, “.pps”, “.ppsm”, “.ppsx”, “.ppt”, “.pptm”, “.pptx”, “.prel”, “.prproj”, “.ps”, “.psd”, “.pst”, “.ptx”, “.r3d”, “.ra”, “.raf”, “.rar”, “.raw”, “.rb”, “.rtf”, “.rw2”, “.rwl”, “.sdf”, “.sldm”, “.sldx”,”.sql”, “.sr2”, “.srf”, “.srw”, “.svg”, “.swf”, “.tif”, “.vcf”, “.vob”, “.wav”, “.wb2”, “.wma”, “.wmv”, “.wpd”, “.wps”, “.x3f”, “.xla”, “.xlam”, “.xlk”, “.xll”, “.xlm”, “.xls”, “.xlsb”, “.xlsm”, “.xlsx”, “.xlt”, “.xltm”, “.xltx”, “.xlw”, “.xml”, “.xqx”, “.zip”
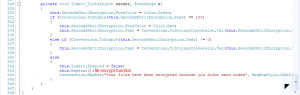
But the key used for encryption is hardcoded(“yourmomgay”), and the encrypt method is Rijndael, as you can see from the screenshots above.
After encrypted, it will add “nRansom2” extention to the encrypted file.
- The unlock key has been changed, but still hardcoded.
The unlock key is “16352”.
Manually Remove nRansom2 Malware & Recover Encrypted Files:
- If not timed up, just input 16352 in the inputbox then click “UNLOCK”, your files are still safe.
- If your files have been encrypted, you can use the key we mentioned(not the unlock key) before to decrypt your files.
- Remove the following directory: C:\Users\[YOUR_USERNAME]\Desktop\nRansom2
- Remove the following file: C:\Users\[YOUR_USERNAME]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\nLocker2.exe
- Clear your computer’s TEMP directory(use some system trash cleaner)
Related MD5:
0DD6F0B54D2B1FECCCBE35F21D199678
95AADF7D79A495DE1010BE9CCB2D51A2
46019D18791820ED845DA9959AB304A4
6DA3CE662F14D60386BEC2D09636FD32
X-Sec Antivirus Detection:
Cloud Engine: Cloud:Trojan.Win32.Ransom
Local Engine: Trojan.Win32.nRansom2.A!GEN(Only for the final payload)
Required Virus Definition Version: 2017.09.25.01(Not released when this blog published)