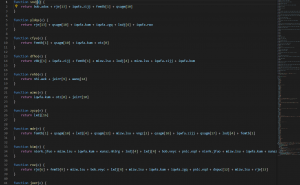
Recently we got a JavaScript file with heavily obfuscated codes. Let’s try to de-obfuscate it and find out what it will do!
![]() As you can see, the original file only has one line(exclude the comment line), its code is also being obfuscated, so first step we need to do is just formatting the code.
As you can see, the original file only has one line(exclude the comment line), its code is also being obfuscated, so first step we need to do is just formatting the code.
After formatted, we noticed the notification from Visual Studio Code:
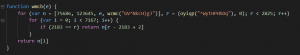
![]() And in the code we care about, there are lots of useless parameters in function call:
And in the code we care about, there are lots of useless parameters in function call:
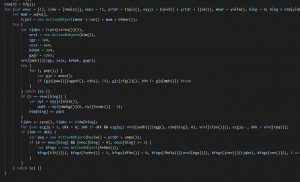
 But we found a function whose parameter is being used:
But we found a function whose parameter is being used:
In fact, this function will return the parameter we passed to it.
We also found a function called “hpd” which has never been called.
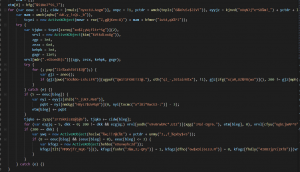
So, after removed such obfuscations, we get the following code(only shows main part):
But, as for the second image, we still need to find out which string will each function return, so it’s time to use Internet Explorer 😉
After function resolve and string replace, we get the following code(only shows main part):
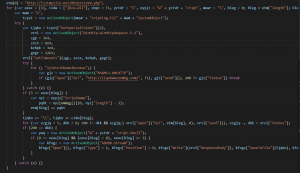 Much more clear than before. Now it’s time to replace const variables, we also found some useless codes in it.
Much more clear than before. Now it’s time to replace const variables, we also found some useless codes in it.
After doing these steps, we finally get the following code(I also provided some comments):
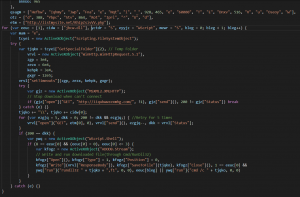 So, the things it will do is clear, this script is just a downloader which will download other malware.
So, the things it will do is clear, this script is just a downloader which will download other malware.
Related MD5:
2CDB7C7DCFDB4289F1FB869F9CA84A00
X-Sec Antivirus Detection:
Cloud Engine:
Cloud:Trojan.Script.Downloader