Today, let’s see a malicious document with obfuscated macro.
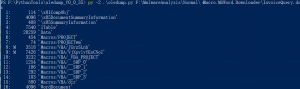
As you can see, the document has two parts contained macro. You can decompile & dump them through oledump or OfficeMalScanner, in this case, I uses OfficeMalScanner to dump macros.
“AutoOpen” function will be executed when opening this document, so we need to analyze this function first.
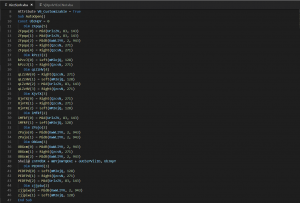
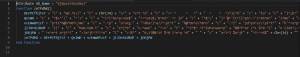
From this image, we can find lots of useless codes, such as:
Dim kPzzJ(2)
kPzzJ(0) = Left(mMIojQ, 128)
kPzzJ(1) = Right(QzcsN, 271)
Define an array, modify its element’s value, but this array is never being used.
After useless code removal, we can only find one line is important:
Shell@ znTPdbX + mBYjUWTQKAI + oUCbzPVliID, UbJHpY
It executes command from the combination of three string variables: znTPdbX, mBYjUWTQKAI and oUCbzPVliID, and uses 0 as its second argument(0 -> vbHide, means the window to execute command is hidden)
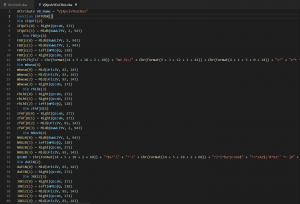
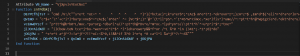
As for the second macro, we can see still find lots of useless codes.
After useless code removal, we can find that we’ll get value of znTPdbX from the only function we found, and this code still contains obfuscation.
For example: Chr(Format(14 + 5 + 18 + 2 + 60)) -> Chr(99) -> “C”
After deobfuscation, it’s still a bit hard for us to get the value of znTPdbX, maybe we should find another way to get the value.
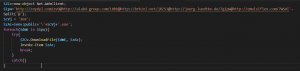
So, let’s run this function in MSOffice! Create a macro, copy and paste the code, use MsgBox to pop-up the value.
We can easily get the value of znTPdbX(contains the command which macro will execute):
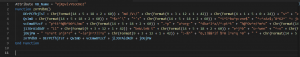
Start a command-line, execute command between two double quotes. Still being obfuscated.
We can find the command contains lots of carets, so, let’s remove these carets and only keep command between two double quotes.
Now command seems a bit more clear.
This command will reverse the string of “xC” then call it.
Now we get the fully deobfuscated command, it’s clear that the command will call powershell then execute another command.
After code beautify, we get the final command. It tries to download malware from five URLs and execute downloaded file when download finished.
Related MD5:
6737171CB822FAAA0C6D5C3AEA12C3DD
X-Sec Antivirus Detection:
Cloud Engine:
Cloud:Macro.MSWord.Downloader