About 2 days ago, we caught an interesting sample which hides its downloader script in the info of document.
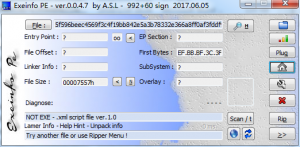 After loaded into Exeinfo PE, it says it’ s a XML script file.
After loaded into Exeinfo PE, it says it’ s a XML script file.
Let’ s open it with UltraEdit.
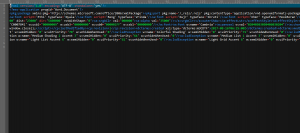 OK, it’ s a true XML script file, but do you mention “<?mso-application progid=’Word.Document’?>” ? In fact, it’ s a office document, the correct file extension for it is “DOCX”.
OK, it’ s a true XML script file, but do you mention “<?mso-application progid=’Word.Document’?>” ? In fact, it’ s a office document, the correct file extension for it is “DOCX”.
If you are using the latest version of UltraEdit, you can simply format the XML script for a much more clear look.
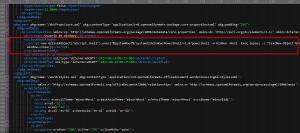 After formatted, we can find the suspicious element called “lastModifiedBy” which contains script, this element stores the name of user who is the last person modified this document.
After formatted, we can find the suspicious element called “lastModifiedBy” which contains script, this element stores the name of user who is the last person modified this document.
This script will download and run a specific powershell script from “HtTP://2584763830:8002/doc/pause.ps1″[I can’t access this URL when I caught this sample]
But what does “2584763830” mean? Well, it’ s just another presentation of IP address, it converts dot-split IP address into a long integer, after converted, it’ s “154.16.93.182”.
In this URL, we can find the hacker uses uncommon IP format & case-insensitive feature to avoid detection.
Related MD5:
EB5FA454AB42C8AEC443BA8B8C97339B