KMSpico is a well-known tool to activate Microsoft’s product, though it has stopped update already and it’s illegal.
And there are lots of repacked version on the Internet, we got a sample which looks a bit more interesting.
This time I want to direct run the sample in Sandboxie.
Like other malicious repacked KMSpico, it drops a malware and run it during installation.
Dropped File Path: “C:\Program Files (x86)\Common Files\InstallShield\Update\ISUSPM.exe”
It’s a heavily obfuscated .NET-based malware, but it’s not the most important point in this blog post.
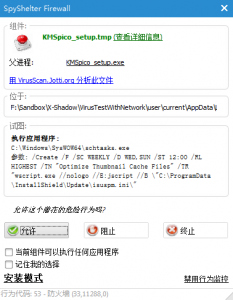 SpyShelter told me the setup file wanted to create a schedule task which will use wscript to run an INI file periodically.
SpyShelter told me the setup file wanted to create a schedule task which will use wscript to run an INI file periodically.
So I found the INI file.
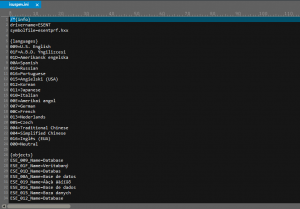 It looks like a INI file on the first sight, but did you mention the first 2 characters? There are the beginning of a comment in some of programming languages like C/C++/JavaScript. And it will be “run” periodically, so script must hide in it.
It looks like a INI file on the first sight, but did you mention the first 2 characters? There are the beginning of a comment in some of programming languages like C/C++/JavaScript. And it will be “run” periodically, so script must hide in it.
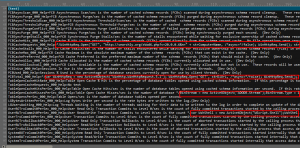 When I scrolled down to browse other parts of this INI file, I found something abnormal. As the image shown above, there are lots of signs of javascript.
When I scrolled down to browse other parts of this INI file, I found something abnormal. As the image shown above, there are lots of signs of javascript.
A better way to find the hidden script is just using some text editor to highlight some keywords.
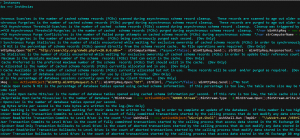 Looks much more better than before.
Looks much more better than before.
This script will download a file and run it with “/VERYSILENT” argument, this argument is widely used by some installers.
Related MD5:
A7728562C9D2D733CAC56F4EEA629AFB
5AF558B541A88697D25063B30C55A536
5587BD55CA9068368A9074491C90E21B
X-Sec Antivirus Detection:
Cloud Engine:
Cloud:Trojan.Win32.Dropper(For malicious repacked KMSpico)
Cloud:Trojan.Win32.Generic(For dropped malware)
Cloud:Trojan.Script.Downloader(For dropped script)